We offer security and compliance services for many types and size businesses, non-profits, and local and county governments. Specifically, organizations with limited staff or limited experience setting up a security and compliance programs, auditing security and compliance, and managing the implementation of security and compliance projects. We know the pace of security and compliance is becoming more rapid and we can help smooth out your transition.
We assess your architecture, data flows, and the security controls and identify gaps against best practices. Assessments are developed in context of business needs, business resources, and data/information security requirements. We provide customized controls reviews such as controls that are in the Defense Federal Acquisition Regulations (DFARS) 252-204-7012, National Institute of Standards (NIST) Special Publication (SP) 800-171A or NIST (SP) 800-53r5, or the Center for Internet Security (CIS) V8 18 controls, and the Cybersecurity Maturity Model Certification 1.02 Framework.
We identify assets, threats and vulnerabilities and determine impact and likelihood of security risks. The risk assessment can be scoped to a particular system or can be broader such as a regulatory framework. A risk register is created, prioritized, and mitigated.
We support incident response plan development and incident response. In the planning phase we work with you to create a customized incident response process for your company based on our experience. When responding to incident we conduct detection and analysis. We perform threat hunting activities by utilizing security tools that monitor network traffic. We also review logs to pinpoint where the incident started and what it is doing. We then move to contain, eradicate, and recover. This includes working with you to take action such as wiping everything and start fresh or continue to monitor for a period to make sure it has been eradicated. This also includes supporting your legal and communications teams in notifying impacted customers or regulatory agencies. After recovery we support post-incident activities. Here we continue to review the process with you, discuss what happened and what should be done to prevent an incident like this happening again.
Our services include testing your web site for exploitable breaches that would allow a hacker to steal client credentials, confirming that network servers and computers are patched and protected, or making sure your staff is trained in the latest phishing and social engineering ploys. Having a penetration test will give you peace of mind knowing you went the extra mile for your security. We are constantly updating our knowledge of the new techniques hackers are using in the real world along with using penetration testing frameworks such as OWASP and NIST 800-115 to make sure we leave no stone unturned. Our tests include intelligence gathering of your company, vulnerability analysis, exploitation and post exploitation. We won’t supply you with an automated scan of vulnerabilities and say this is what you need to fix, we uncover and act on the vulnerabilities and exploit them along with other manual means that could be missed with an automatic scan. Not sure how to fix the vulnerabilities or exploits we find? We can help. We will provide detailed recommendations on how to mitigate these issues and offer another test to make sure our recommendations have been implemented and are working.
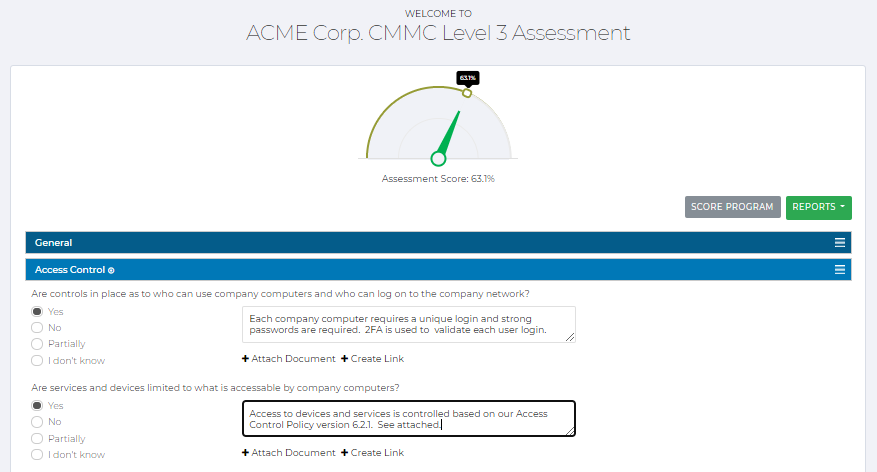
(e.g. DFARS, CMMC, SOC 2)
We work with companies to aid compliance with any one of a number of frameworks. For example, over the last several years the Aerospace & Defense (A&D) industry has a requirement to comply with Defense Federal Acquisition Regulation Supplement (DFARS) 252.204-7012 and NIST SP 800-171A requirement, and more recently the Cyber Maturity Model Certification (CMMC) Framework 1.02 controls. Other companies have to comply with System and Organization Controls (SOC), and SOC 2 to look at the design and effectiveness of controls through the SOC lens for Service Organizations: Trust Services Criteria. We tailor the compliance services to meet attestation requirements.
We have designed policies for medium and small business. We assess your current policies to determine what you already have and the gaps against our policies. Our policies are customized to meet the requirements of DFARS 252.204-7012 & NIST 800-171A, HIPAA, and GDPR. Each policy also has built in best practice controls from the 18 CIS control families and expanded to the Cybersecurity Maturity Model Certification (CMMC) Framework 1.02 controls, . Policies include easy to understand procedures. Each policy also includes individual action plans. The policies deliver to you and refined through our change process also include a 1 Year Calendar and cross-policy Gantt chart with activity timing and roles & responsibilities. Our policies are refreshed on an ongoing basis. We also offer customized policies for staff/end-users.
Our customers have customers. Our customer's customers have security and compliance requirements that are delivered with short turnarounds typically ranging from several days to several weeks. These audits demand attention. We support you by understanding the requirements, including what may have changed in the last year. We review the changes with you and then develop a strategic response. If any of the audit questions indicate that a modification to security strategy or controls is required we will start working with you to identify what needs to change in your security environment.
We identify your security requirements and the requirements you have for flowing these requirements down to your vendors. Do your vendors pay the same attention as you do to security? The flow down requirements are integrated into your Master Services Agreement requiring your vendors to understand your security expectations. Typical inclusions are having security policies, a System Security Plan (SSP), conducting penetration tests of their environment, having a designated individual to coordinate on security matters, and being able to respond to security audits or incidents.
Businesses have legal obligations to protect the privacy of stakeholder information. There are new and changing regulations. Some companies have to comply with The Health Insurance Portability and Accountability Act (HIPAA) regulations, others with the California Consumer Privacy Act (CCPA), Virginia’s Consumer Data Protection Act (CDPA), or State data breach laws. If you are doing work with Europe, then the General Data Protection Regulations (GDPR). We help companies assess and understand their obligations and implement appropriate compliance measures and controls.
We also provide other critical security services. We develop Business Continuity and Disaster Recovery Plans, Access Control Strategies, Data Classifications, Data Flow Models, and Insurance Audits. Safe Harbor strategies for Connecticut, Ohio, and Utah.
*The deliverables are unique in the industry and customized for It's Just Results clients
Our work is highly collaborative and we take great pride in fitting in with our client environment and culture. Each project and environment is different, but because we have worked in so many environments we understand what works and what does not work. As a result, we have developed standards for how we approach projects. This systematization keeps your costs down and results in a higher quality deliverable.
We have also productized our security and compliance focused policies for a number of industries. We then vary the amount of support our clients needs for supporting policy development and deployment. Our policies are structured to work in a number of environments, such as Defense and Aerospace (DFARS), Federal Civilian (NIST 800-171), and Health (HIPAA). In addition, we have integrated Center for Internet Security (CIS 20) Control requirements into the policies we tailor for you.
We take on a variety of roles. It depends on your needs. What does not change is our commitment to providing you with results, creating a friendly and collaborative experience, and aspiring to continue as your trusted advisers.